APRA — an independent statutory authority that supervises institutions across banking, insurance and superannuation — has promised to increase cyber security regulations, even going as far to extend its regulatory reach from 680 entities to over 17,000 entities.
One would that think such “regulatory intervention” is based on evidence of its existing cyber security regulation — CPS 234, which came into effect in July, 2019 — being ineffective. However, one would be wrong.
Despite APRA itself admitting that no regulated entity had suffered a material cyber security breach, regulated entities will be forced to spend time and effort on additional cyber security controls. Under Australia’s Notifiable Data Breach Scheme, companies that fall under the Privacy Act must notify the federal government if they suffer a material data breach. (And, yes, cyber security breaches may not necessarily be data breaches.)
Instead, APRA’s Geoff Summerhayes pointed to other industries’ — industries over which APRA has no control — cyber security woes to justify the increased regulation. Likewise, justification included “increased attack surface”, COVID-19, geopolitical tensions, and increasing complexity in supply chains. Unsurprisingly, similar reasons were given when CPS 234 was announced. I’m reminded of Bruce Schneier saying, “Attacks only get better; they never get worse”. In the case of regulatory intervention, “Regulations only ever increase; they never decrease”.
As I wrote previously, politicians love an emergency; emergencies give politicians, bureaucrats, and institutions a chance to increase their power, influence, and, in this case, regulatory reach. Geoff Summerheyes mentioned COVID-19 in other industries, but, yet again, admitted that COVID-19 hadn’t brought about more attacks on financial services.
One expects to read quantitative evidence of the need for APRA to increase cyber security regulations; however, none was forthcoming.
APRA’s 2020-2024 Cyber Security Strategy
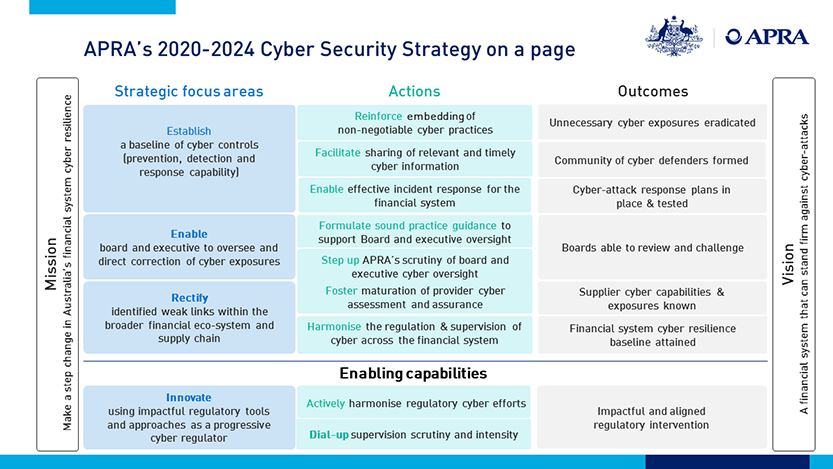
The strategy focuses on three areas:
Establishing a Baseline of Cyber Controls
This is perhaps the most concerning. Who knows which cyber controls are the most appropriate, cost effective, and manageable? A company? Or bureaucrats in Sydney? Where does the knowledge lie to secure a company’s IT systems? With bureaucrats who don’t understand the company, its risk appetite and tolerance, & IT systems? Or with internal security professionals who understand the company its risk appetite and tolerance, & IT systems?
Ironically APRA’s mentioning of the complexity of supply chains is the exact reason why an approach to a set of baseline controls cannot work. Technology is too complex, moves too quickly, and there is far too much nuance.
A quick glance as the ASD’s Essential Eight shows the problems with such security control baselines:
- Application patching. Want to take away that business application that’s no long supported by the vendor? The application that brings in $10 million a year? Good luck.
- Application control. Good luck restricting application execution on developers’computers. This is extremely difficult to manage due to developers needing access to development tools, often within a short time period.
Ironically, and unsurprisingly, the federal government won’t even enforce a cyber security baseline for its own departments. Regulation for thee but not for me. Moreover, anyone who’s ever dealt with PCI-DSS — not a regulation but rather standard enforced by credit card providers through banks — understands the problems with security baselines:
- Too much time spent on unimportant controls, such as TLS cipher suites over internal networks.
- Companies simply architecting their systems to avoid/lower “regulation”.
- Audits vary based on the auditor, often someone young who doesn’t understand how businesses function or someone old who doesn’t understand serverless architectures. Talk to any QSA, and they’ll tell you the same: Auditors work in varies levels of grey rather than black and white. Some auditors accept some controls/exemptions, others don’t.
Granted, any such set of baseline controls must have a risk-based approach, and there must be a risk-based exemption process to document why certain controls cannot be implemented. However, there are serious problems attempting to define a baseline set of controls.
Enabling Boards and Executives of Financial Institutions to Oversee and Direct Correction of Cyber Exposures
I don’t mind this aspect too much. I don’t mind APRA formulating risks in a manner in which board members can understand. If we are to have cyber security regulation, then incentivising boards/CEOs is far more preferable than descriptive baseline controls.
Rectifying Weak Links within the Broader Financial Ecosystem and Supply Chain
“To achieve this, APRA will engage with a selection of suppliers, auditing associations and financial entities to develop stronger third-party provider assessment and assurance practices for use by APRA-regulated entities”.
I’m not sure what APRA intends to do. The players in the game — third party services providers — are well-known in the industry. Currently contracts between companies and third parties define the level of security of third parties. Many of these contracts were signed years ago — before cyber security became more important — and hence the contracts often do not address cyber security or lack clauses such as the right to audit, the third party’s cyber security maturity, the right to conduct a penetration test against services in the contract, and the availability of logs during security events that may turn into security incidents. And there is a lot more nuance between software contracts and managed infrastructure contracts that I won’t mention.
It’s difficult for companies to negotiate with third parties. Third parties are often US companies with massive clout. Do you think you can force AWS to make significant changes? No, of course not.
I can’t comment any further without details. I doubt APRA will make significant progress based on my knowledge of the industry. It’s difficult to regulate third parties upon which the federal government relies.
A Word on Regulation
Once the government has its foot in the door, the flood is inevitable. Regulatory agencies are similar to businesses: They will always expand, rarely decrease, with CEOs and board members looking to increase their power and influence.
Individuals within regulators are incentivised never to solve the problem they’re in place to solve. Why would they? Then the money would dry up. APRA admitted to no material cyber security breaches within the financial services industry, and yet APRA is imposing more regulations upon the industry and increasing the number of entities under its control.
Is APRA solving a problem? Or is APRA creating a problem to be solved? Undoubtedly cyber security is an important issue for businesses. But is APRA best placed to tell businesses which security controls they need?
The regulatory capture of the cyber security industry in Australia continues. If you care about mass surveillance, the federal government’s increased confluence with private companies — from which the government receives Australians’ private data en masse — should concern you.
More government involvement in the industry can only lead to more mass surveillance, as I pointed out in my initial blog post.